Learning pwndbg Debugging Through a Reverse Engineering Challenge from CyberSpace CTF
Today, I’ll demonstrate gdb debugging techniques in a Linux environment using a basic reverse engineering challenge from CyberSpace CTF, while also showing how it can effectively replace Cheat Engine’s basic functionality.
Here we go !
0x01. Install pwndbg
First, we need to install pwndbg, a robust memory debugging and manipulation tool that enables us to modify values at specific memory addresses during runtime analysis. The tool is :pwndbg
Just see README.md, what you will get interested is as follows:
1 | git clone https://github.com/pwndbg/pwndbg |
Before proceeding with pwndbg installation, ensure that you have gdb (GNU Debugger) properly installed on your system as it serves as the foundational debugging framework.
Here we can see that we have successfully completed the installation of pwndbg.
0x02. Debug process
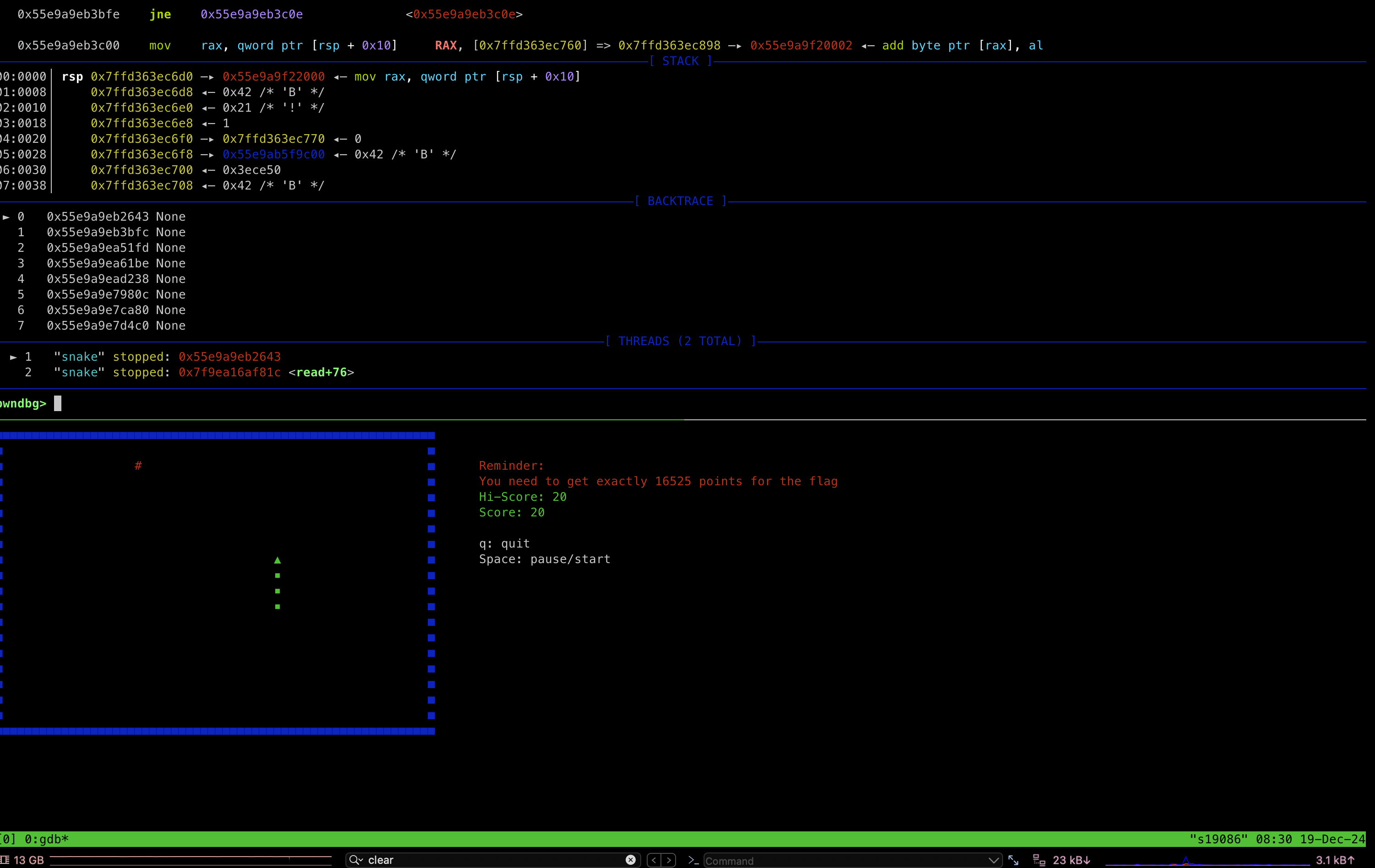
Upon executing the snake ELF binary, we’re presented with a Snake game implementation. The right-side notification indicates that flag acquisition is contingent upon reaching a specific score threshold. Instead of conventional gameplay, we’ll leverage reverse engineering techniques to bypass this scoring mechanism and obtain the flag.
First, let’s play the game until we reach a score of 20 points (0x14 in hexadecimal). Our strategy will then focus on identifying memory addresses containing the value 0x14 (20 in decimal) for manipulation. Given that local variables are predominantly stored in the stack segment, we’ll concentrate our analysis on stack-based variables.
type command as follows:
1 | search -t dword -w 0x14 |
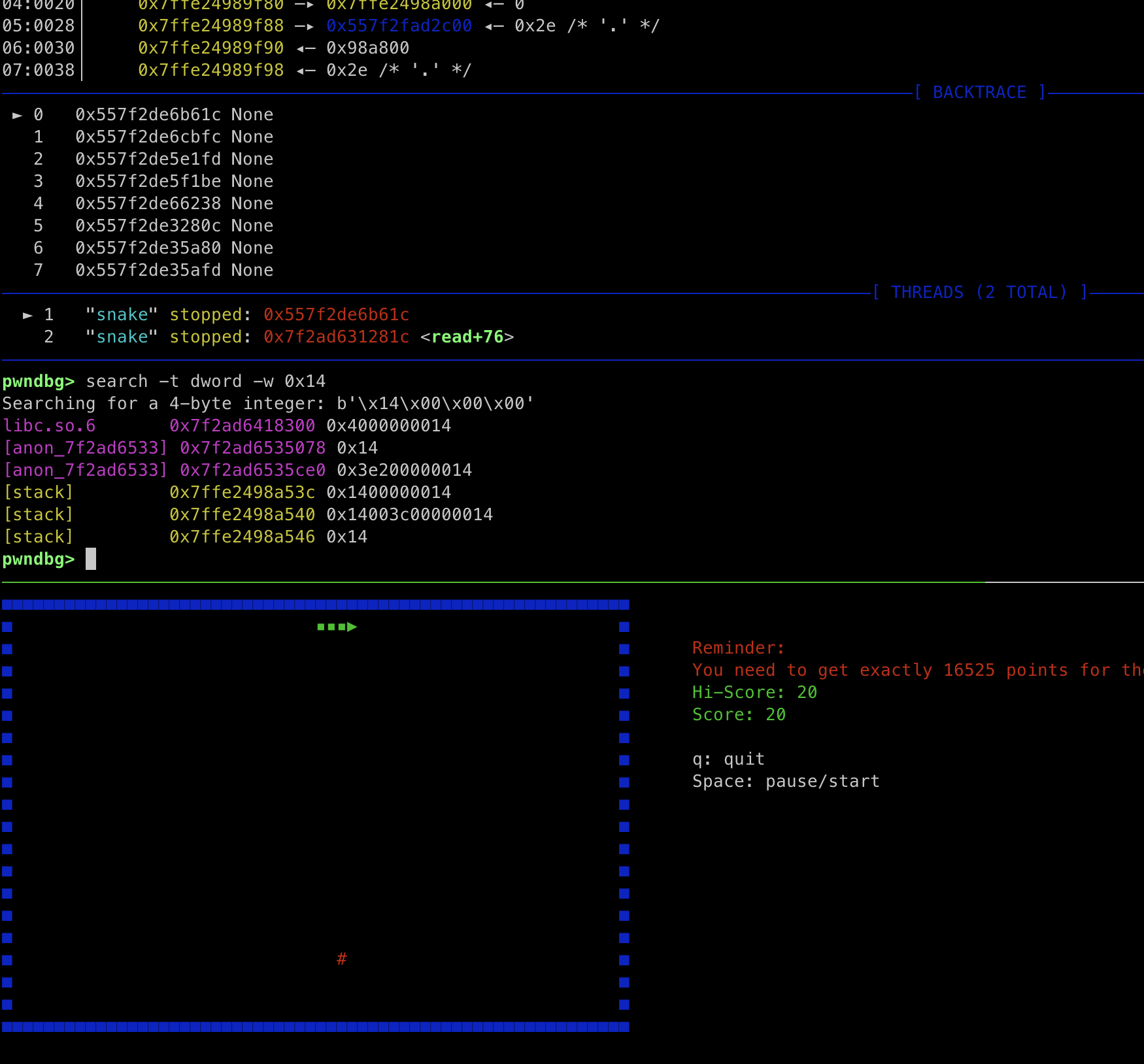
Here we can see that we’ve successfully located several addresses, but we’re not yet certain which one is the specific address we need to modify.
To identify the correct memory location, let’s proceed with the game until we reach a score of 40 points. We’ll then conduct another memory scan to cross-reference with our previous findings, which should help us isolate the actual score variable’s address.
1 | search -t dword -w 0x28 |
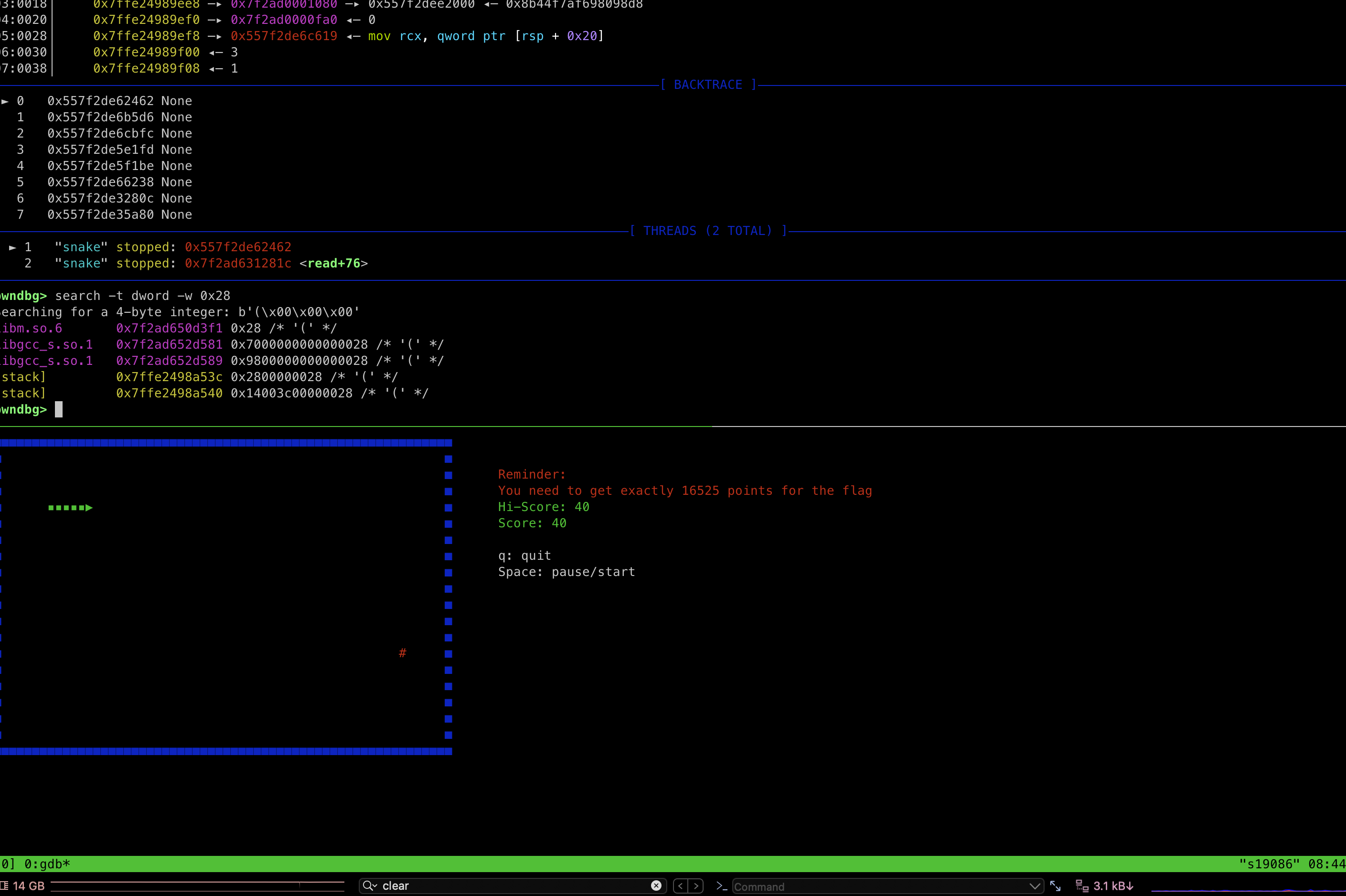
We’ve identified two recurring addresses from our previous search: 0x7ffe2498a53c and 0x7ffe2498a540. These addresses have consistently tracked our score changes.
OK, now it’s time for the magic moment! Let’s modify the values at these two addresses to our desired number: 16525 in decimal (0x408d in hexadecimal).
type command as follows:
1 | set *(size_t*) 0x7ffe2498a53c=0x280000408d |
Here we should note that we only need to modify the last four bytes, as a double word corresponds to exactly four bytes. the same as 0x7ffe2498a540
the type c to continue our process.
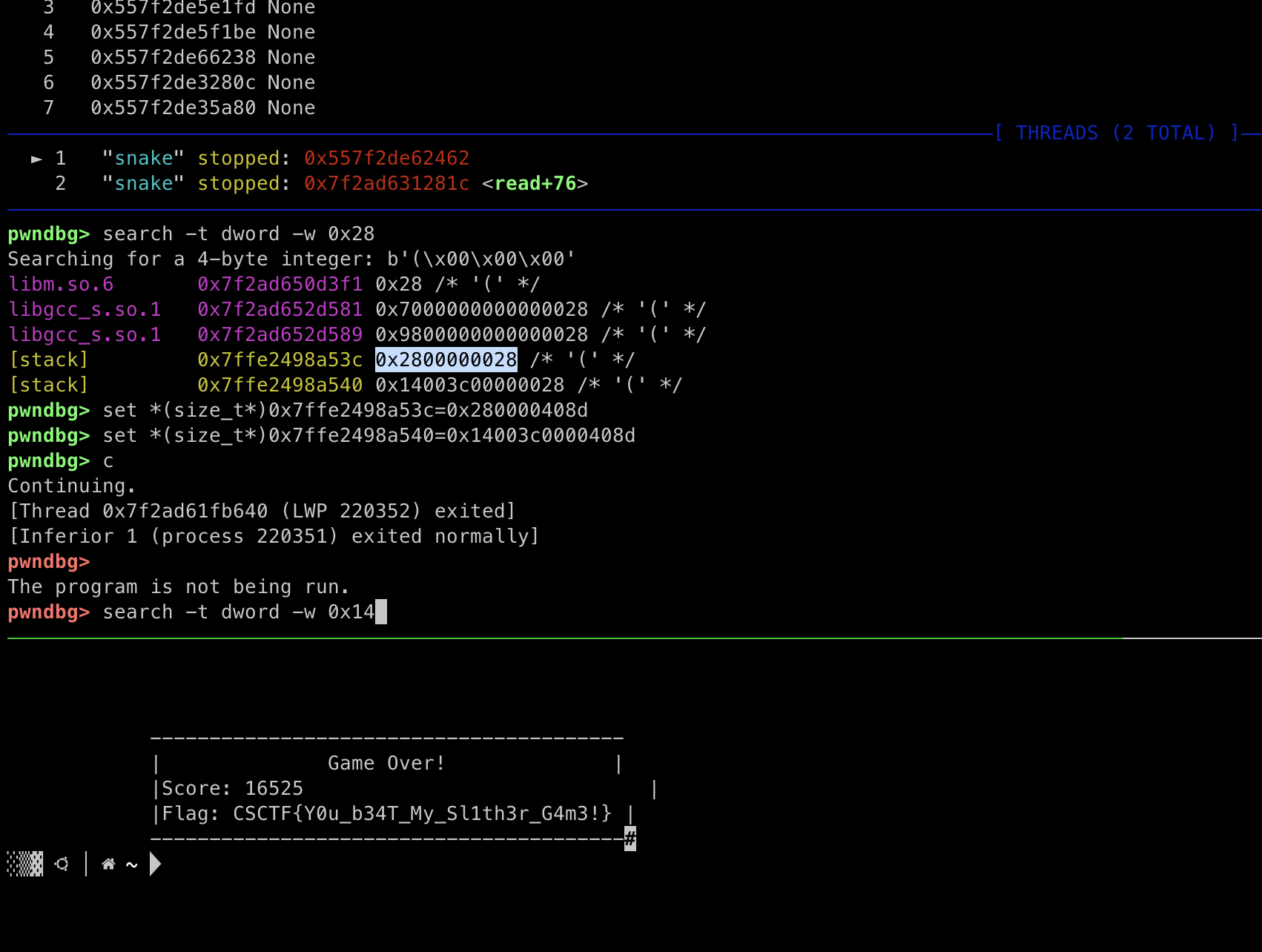
Flag: CSCTF{Y0u_b34T_My_Sl1th3r_G4m3!}
Thanks for reading!!
- Title: Learning pwndbg Debugging Through a Reverse Engineering Challenge from CyberSpace CTF
- Author: zder
- Created at : 2025-01-15 03:06:06
- Updated at : 2025-01-15 03:06:06
- Link: https://fluxword.net/2025/01/15/snake/
- License: This work is licensed under CC BY-NC-SA 4.0.